Stack traces give a lot of information about the running software. The software version deployed on a server can be critical for an attacker during a penetration test. We developed the X41 BeanStack API which accepts any Java stack trace, searches a database of known products, and returns details about the software in use. Please note, this is currently in BETA, so it can stop working or work incorrectly at any time.
Try It
Actions speak louder than words, so why not try a query?
Stack trace:
Burp Extension
Using this website every time would be rather tedious, so we developed an open source Burp extension which automatically looks up any stack traces. It locally filters out Java stack traces from your Burp proxy traffic and submits only the relevant data.
To install the extension, download the latest release from GitHub. In Burp, open the “Extender” tab, make sure you are on the subtab “Extensions”, and click the Add button. The extension type is Java, select the file you downloaded, and set the other options as desired.
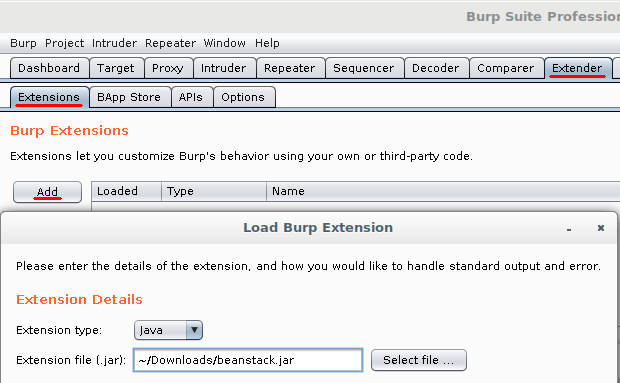
Please note that you need the Pro version of Burp for our extension to work correctly. In the free version, there are no ‘Issues’, which is where the fingerprinting results would be shown.
Extension Usage
After installing, the extension works automatically in the background. When it finds a trace, it submits it asynchronously. If the submission comes back with no results, it does not bother you. If it finds results, it logs an “issue” in the background that you can look at when you want to. Issues can be found under the Dashboard (top right corner), or per website in the Target » Site Map tab.
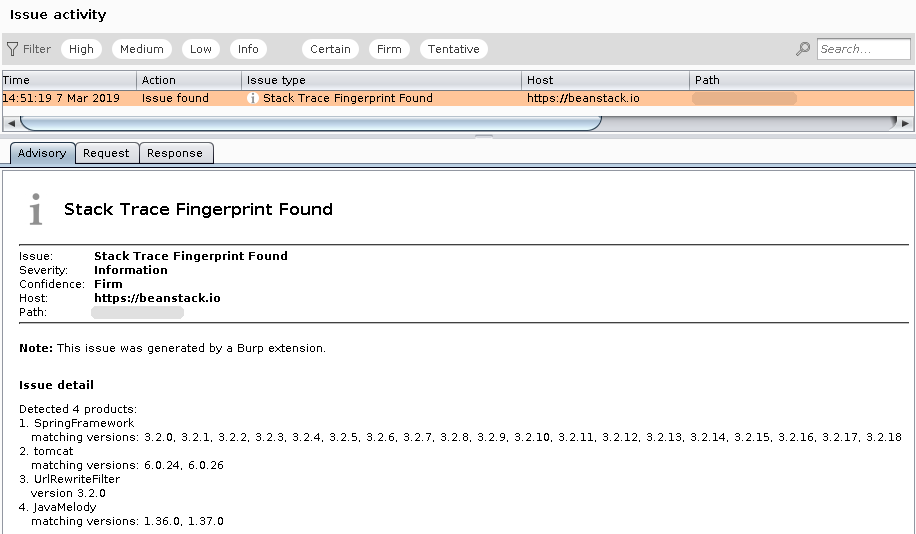
Some settings can be controlled through the BeanStack menu. For documentation about each setting, see the settings page.
API Keys
In case you want to get more out of this, you need an API key, which you can register for here. This will increase the API rate limit, give you CVE information, and allows you to submit BLAKE2b-hashed traces.
If you need additional output or another API for whatever you want to do, feel free to contact us.
Bug reports
Any bugs can be reported as GitHub Issue, or you can use the contact information as mentioned on this website.
How does it work?
Eric gave a lightning talk at 30C3 about the idea. A Java stack trace contains information about the whole call stack, including function names and line numbers. X41 BeanStack matches these function names and line numbers against a huge database of software source code to determine the software version in use. This information can then be used in a penetration test to determine vulnerabilities and help to faster exploit the attacked systems.
About X41 D-Sec GmbH
We are a renowned expert provider for dedicated high quality security research, application security services, penetration tests, and full red teaming. Having extensive industry experience and expertise in the field of IT security, a highly effective security team of world class security experts enables X41 to perform premium security services.
Fields of expertise in the area of application security are code reviews, binary reverse engineering, and vulnerability discovery. Custom research and high quality IT security services are core competencies of X41.
More information is available on the X41 homepage, contact us via info@x41-dsec.de.